Java Code Vulnerability Example
In this variation the attacker tries to get information like an error code and a message from the database. FileInputStream fis new FileInputStreamCtemp userinput.

Insecure Deserialization In Java Apache Struts Example Video Semmle Blog
After some research I found a similar vulnerability on another functionality of the application which bringed me around 6k payouts in total.

Java code vulnerability example. For example in July this year a critical vulnerability CVE-2021-35464 in ForgeRocks OpenAM stemmed from unsafe Java deserialization in the Jato framework used by. First of all you need to look closely at the design of your application and determine if you really need the data. The following are the APIs most commonly used for executing an arbitrary string as a SQL query.
Join For Free. As shown below it begins with ac ed when viewed in hexadecimal format and rO0 when base64-encodedPortSwiggers proxy tool BurpSuite flags serialized Java objects observed in HTTP requests and the Java. But when youre working on a larger project or numerous.
The tmp example file contains a serialized Java object. In this insecure deserialization java example we will explore step-by-step how we can exploit insecure deserialization in Java. A case which is created within the malicious expression returned nt authoritysystem from the Java code.
I bufferi 7. SystemoutprintlnImportant data importantData. 2 SLEEP 5 Query.
If youre working on a small project that might be an easy feat. String userinput bootini. Which returned a successful and pure Java code injection.
Serialized Java objects begin with ac ed when in hexadecimal format and rO0 when base64-encoded. Int buffer new int10. Recently I came across few Java.
SonarQube is a web-based tool that can help developers produce code free from security issues bugs vulnerabilities smells and general issues. For example the exposure of unique identifiers in your system is a Java security vulnerabilty if that identifier can be used in another call to retrieve additional data. Then we will look at the implications of a successful attack.
Is being merged with another or cloned into a new object. You could carefully work through your code to find any issues. Public class Overflow public static void mainString args int importantData 1.
This article represents top 4 security vulnerabilities related coding practice to avoid while you are programming with Java language. In the case of our Java application with the Eclipse IDE working with Kiuwan and Checkmarx we have the possibility of integrating the tools on the IDE itself so while we are developing our Java classes and interfaces we can also run the SAST checks. Through a simple GET request an attacker could send a.
The code defines a class with the name NormalObj which does nothing but print the name attribute when the deserialization happens. In this tutorial well explore how an attacker can use deserialization in Java code to exploit a system. Java deserialization vulnerability example.
This can result in interesting security issues like Javascript prototype pollution vulnerabilities mass assignment vulnerabilities etc. This can for example happen when the application was expecting to receive configuration data or payload containing serialized Java objects. This vulnerability applies to Java deployments typically in clients running sandboxed Java Web Start applications or sandboxed Java applets in Java SE 8 that load and run untrusted code eg code that comes from the internet and rely on the Java sandbox for security.
Moreover by double-clicking each problem reported a Java. Error Based SQL Injection. Kiuwan displays information on the vulnerabilities we have in the Problems view.
For int i 0. Its a code execution vulnerability that will give us full access to the target computer. NIST publishes 50kish vulnerable code samples in JavaCC is officially krad NIST has published a fantastic project its been out since late December but I only just became aware of it where theyve created vulnerable code test cases for much of MITREs CWE project in Java and cc.
These words usually indicate that an object dict map etc. Well start by looking at some different approaches an attacker might use to exploit a system. Systemoutprintlnafter buffer overflow.
JavaioFileInputStream javaioFileOutputStream javaioFileReader javaioFileWriter Code vulnerable path traversel. For example in July this year a critical vulnerability CVE-2021-35464 in ForgeRocks OpenAM stemmed from unsafe Java deserialization in the Jato framework used by the application. Select emp_id first_name last_name from tbl_employee where empId2 SLEEP 5 In the above example query execution will pause for 5 seconds.
Finally we will look at some best practices to help avoid these types of attacks. _merge in LoDash _clone in LoDash. Exploiting a Code Execution Vulnerability.
How to correct vulnerabilities in Java code. In this section we are going to have a more advanced look at Metasploit and we are going to see how to use it to exploit a vulnerability that exists in a certain service.

Protecting Against Command Execution Attacks

A Sample Java Code And Its Corresponding Jimple Code Download Scientific Diagram

Why Findsecbugs Report The Vulnerabilities Type Hard Coded Password In The Code Segment Of The Imported Library And Class Name Definition Issue 617 Find Sec Bugs Find Sec Bugs Github

Are You Guilty Of Embedding Credentials Into Your Source Code Xcalibyte Software Application Quality Compliance Security
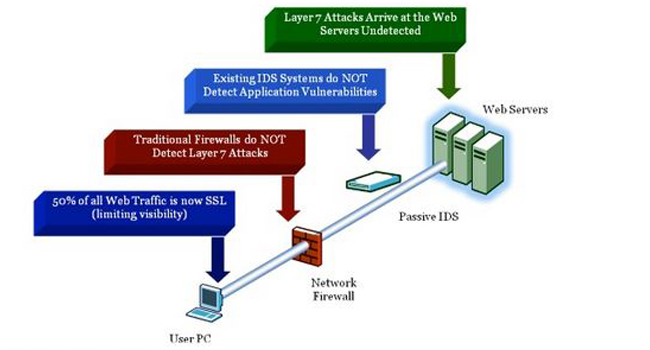
Security Vulnerabilities In Java Based Web Applications 3pillar Global

Top 25 Coding Errors Leading To Software Vulnerabilities Waverley
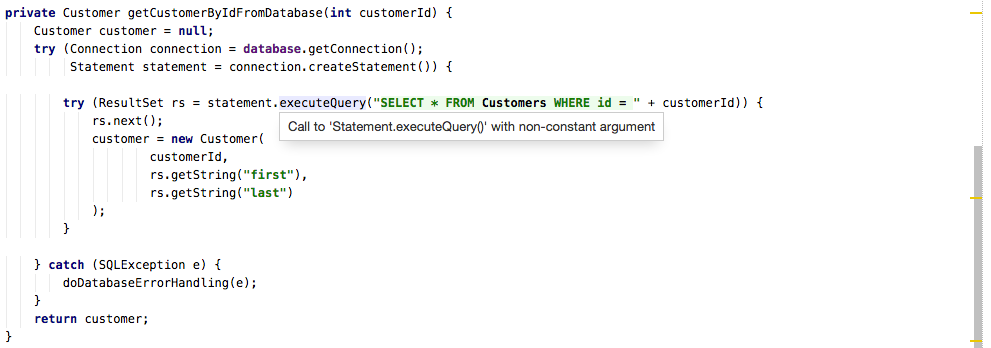
What To Look For In A Code Review Security The Upsource Blog
Apache Struts Remote Code Execution Vulnerability Cve 2017 5638 Devcentral

Sql Injection The Equal Opportunity Vulnerability Infosec Resources

Real Life Examples Of Web Vulnerabilities Owasp Top 10

Secure Coding How To Eliminate Code Vulnerabilities For Good

Why Findsecbugs Report The Vulnerabilities Type Hard Coded Password In The Code Segment Of The Imported Library And Class Name Definition Issue 617 Find Sec Bugs Find Sec Bugs Github

Find Security Bugs The Open Source Java Static Analysis Tool Gosecure

Static Application Security Testing Sonarqube
Java Vulnerability Java Code Analyzer

Static Application Security Testing Sonarqube
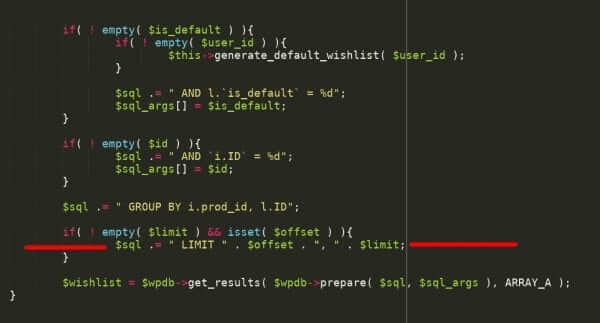
Owasp Top 10 Security Vulnerabilities 2021 Sucuri
Https Help Veracode Com R C Sc Java
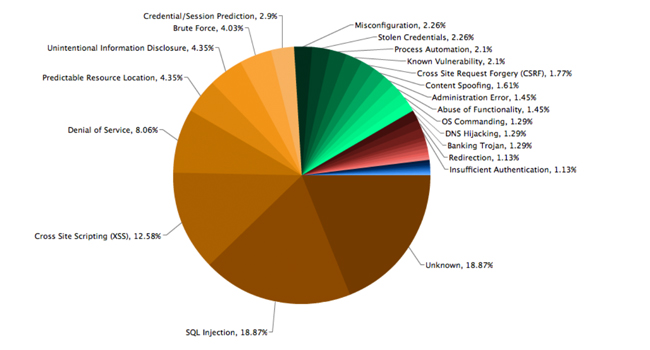
Security Vulnerabilities In Java Based Web Applications 3pillar Global
Post a Comment for "Java Code Vulnerability Example"